Password Reset Best Practice
Summary In the era of modern desktops and biometric security we constantly find ourselves less reliant on our passwords to access our accounts. To name a couple: PINsFingerprintFacial Recognition Although this helps make our sign-in experience more convenient, we find...
OneDrive considerations and tips
Summary Almost all data now is stored online either in OneDrive or SharePoint. As the files and documents are online, we need to make sure that we can always access them. The OneDrive sync client is what allows this to work and keeps...
Bitlocker Prompts
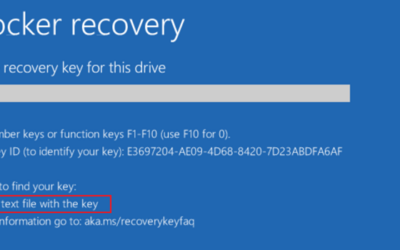
Bitlocker Prompts You may have turned on your device and notice this following screen: This may look scary at first but here at CenCom Solutions we have come up with a fix to get you working again. PC Steps Remove the power cable out the back of the PC.Leave it for 10...
Remote Desktop Advice
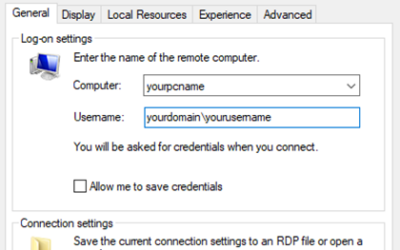
You may be working from home due to the current COVID situation, below is some helpful tips to make sure your able to remote to your work PC. Prerequisites Remote computer needs to be turned on and connected to the...
Best Practice for data management in SharePoint
How to sync sites and find out more Microsoft provide a rounded and helpful article with several videos that cover the basic usage of SharePoint. You can follow the link below to see how to sync SharePoint sites to your local device. Sync SharePoint Site Syncing data...
Do We Need Cables?
Wireless networks have nearly as fast headline connection rates as cables, do you really need a cabled network any more?
Encrypt USB Drive
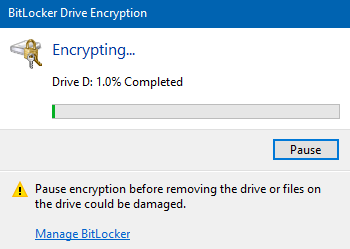
BitLocker on Windows BitLocker will encrypt your USB drive and then require a password to be entered whenever it is connected to a PC. To get started using BitLocker, connect your USB drive to your computer. Right-click on the drive and click on Turn on...
Certifiable
CenCom Solutions has achieved Cyber Essentials certification. We have discussed Cyber Essentials before and we have been advising our clients to become certified for at least a couple of years. Well we are going to practice what we preach and have gained...
What Is Multi Factor Authentication
The security of two-step verification lies in its layered approach. Compromising multiple authentication factors presents a significant challenge for attackers. Even if an attacker manages to learn the user's password, it is useless without also having possession of...
Outlook Tips 2
Delay Sending Have you ever clicked send and then suddenly realised you forgot the attachment, or included a recipient who should not receive that email. You try to catch it but it is too late, it has gone. To mitigate against that there is a setting in...
CenCom are proud of our Managed Backup
CenCom Solutions Managed Backup & Recovery Backup and recovery made simple. When the inevitable happens, rest assured that you can quickly get back to a stable state. Whether it comes from a technology failure, a natural disaster or just user error,...
Image in that
Image in that We all want to make our work stand out and many times you will have wanted to insert a fun or informative image into a word or PowerPoint file. Some of you might remember the good old days where office came with a second CD which had clip art gallery on...
General Data Protection Regulations and your business
This is an enhancement to existing privacy regulations in the UK currently enforced by the Information Commissioners Office under the UK Data Protection Act.
The Regulation is a European one however because it comes into force before the UK leaves it will be relevant and UK government has already said they would expect to implement it in UK law anyway.
What the GDPR is that?
What the GDPR is that? From a personal point of view many of the changes which this brings are a good thing. People have for many years now been taking personal information online and in other methods from us and then using it is ways we have not agreed with and many...
ALERT from CenCom Solutions
WannaCry RansomWare. Over this weekend, you will probably have heard of the outbreak on Friday of a new strain of ransomware called WannaCry. Much has been said of it being caused by out of date computers and systems however this is not the whole story. The ransomware...
Threat Alert!
Be Aware! CenCom have recently been made aware of a spoof email that’s been sent to several client's email accounts. The email invites recipients to download an invoice from a malicious link. Some of these emails claim to be from senior members of clients or members...
Search and Ye shall find
Search Finding things, you need is becoming increasingly complicated with 1000’s of emails and documents stored in a variety of places. Many users struggle to find things and there is a limit to the our ability to remember where and things were to try and search...
Take Note
OneNote to rule them all. Microsoft Office has included OneNote for some time now and it has improved with each iteration however many of you may be unfamiliar with the office products outside of the Word, Excel, Outlook and PowerPoint staples used by most of you. We...
When is a restart not a restart?
I thought I restarted already! Are you shutting down your laptop or computer daily, only to have IT audaciously ask you to restart it? You're certain you've already turned on your device that morning. Well, there's a valid reason for this request, and the following...
Creators Update
The New Windows 10 and you Many of you will have had the new “creators update” deployed and many more will have it delivered over the coming weeks so we thought we would explain what is happening and why some inconvenience may be a good thing. Firstly, as you may be...